Otter Leak
Author: Lucian NitescuContest: OtterCTF 2018
Description:
We found out that one of the Otters been leaking information from our network! Find the leaked data.
Format: CTF{flag all uppercase}
Stats:
200 points / 45 solvers
Solution:
On this challenge, I was provided with a .pcap file which contained packets form an internal network. My first step in every pcap file is to lunch Network Miner tool and take a look at what it retrieves. Here I discovered the following files:
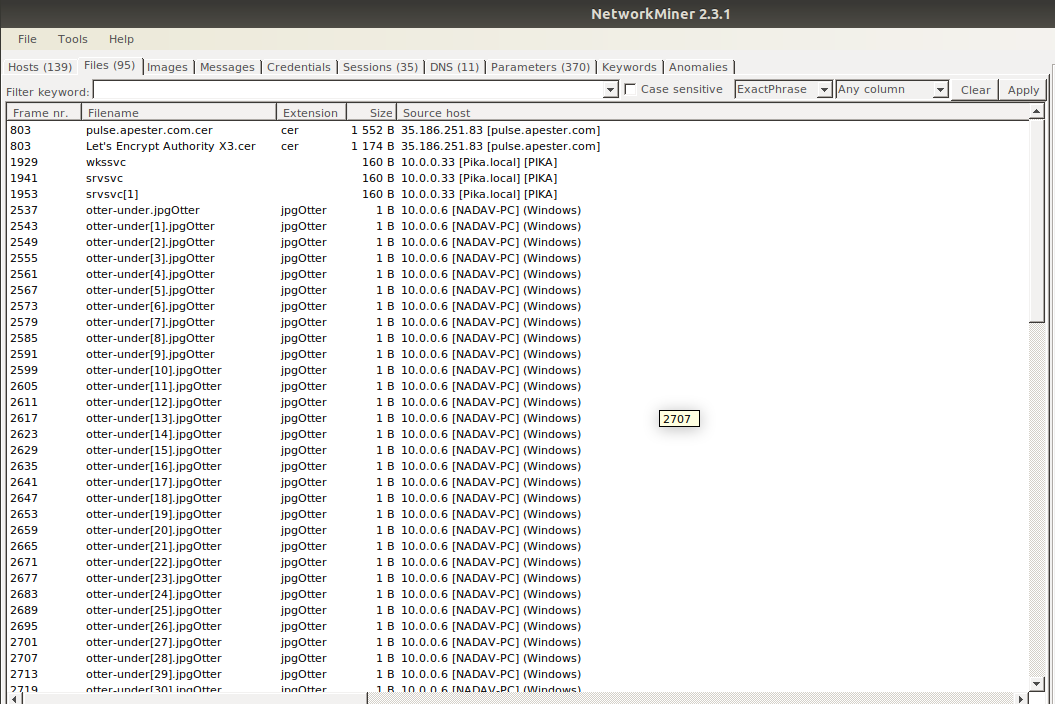
Because Network Miner is a good tool, but not perfect, I had to launch Wireshark and extract all the files sent by 10.0.0.6 host over SMB protocol.
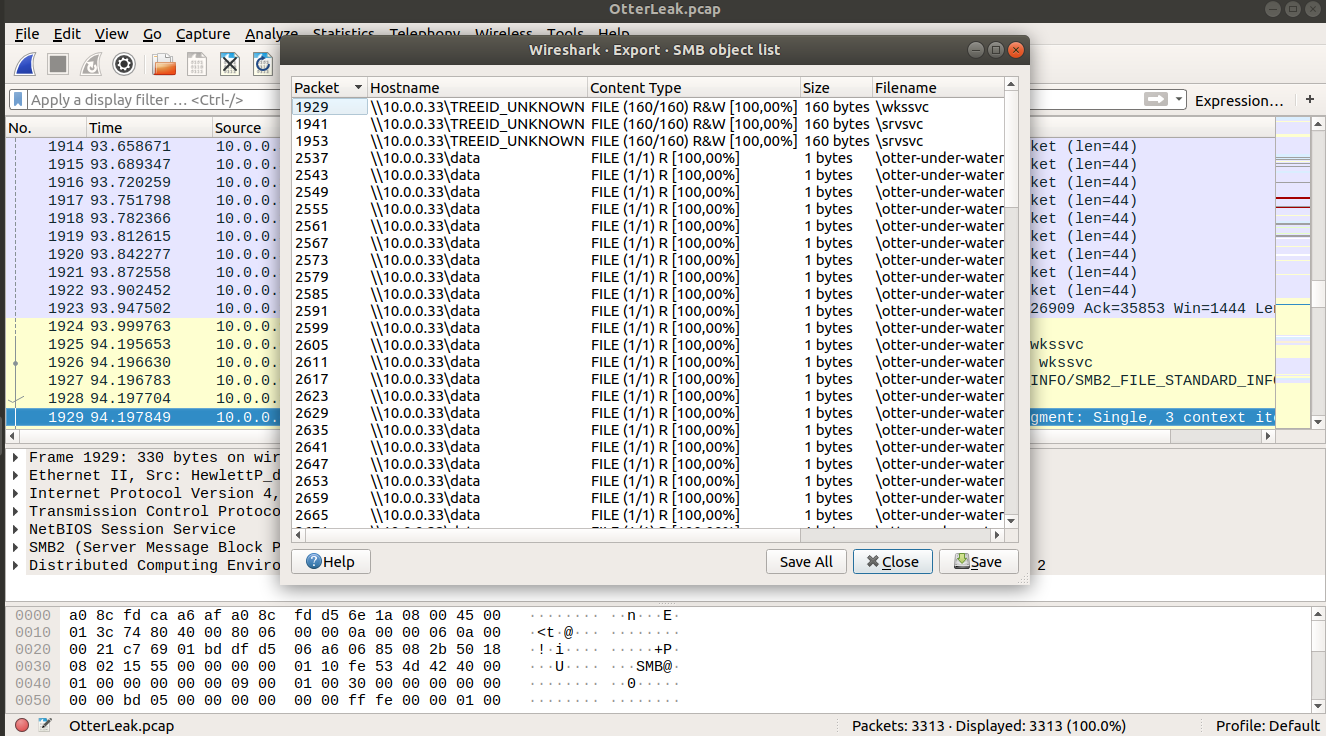
Output of the Wireshark file retrieval:
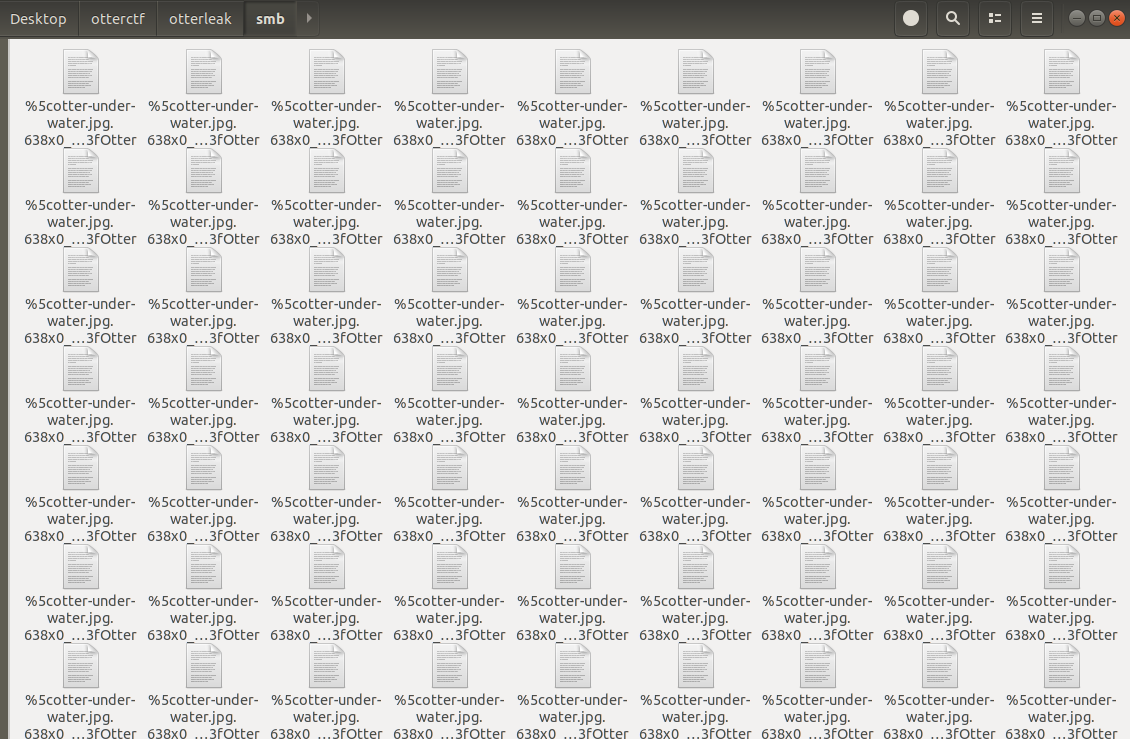
At this point, I discovered that all files are of .jpg extension but contain only one character. Let’s read them all at once!
As you can see in the following image, I got on first row a string which looks like a base64 encoding:
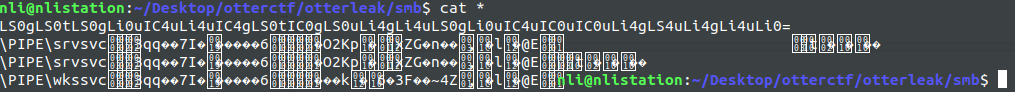
I decided to decode my string, and I obtained the following Morse code:
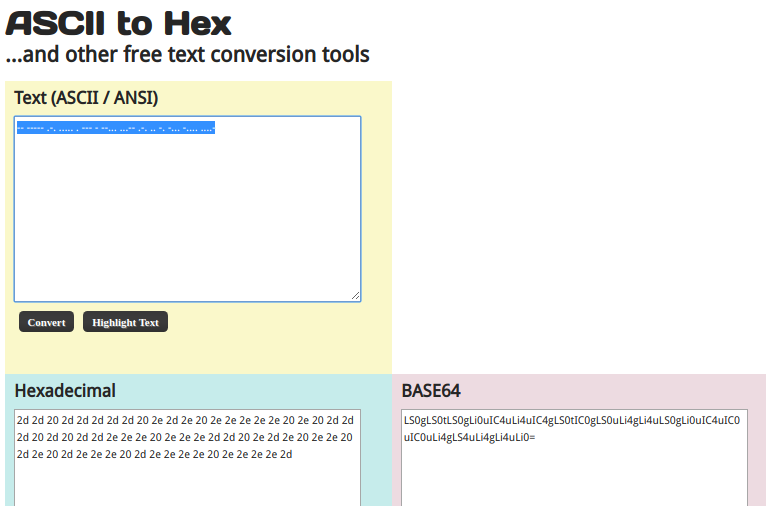
I decoded my Morse code and obtained the flag:
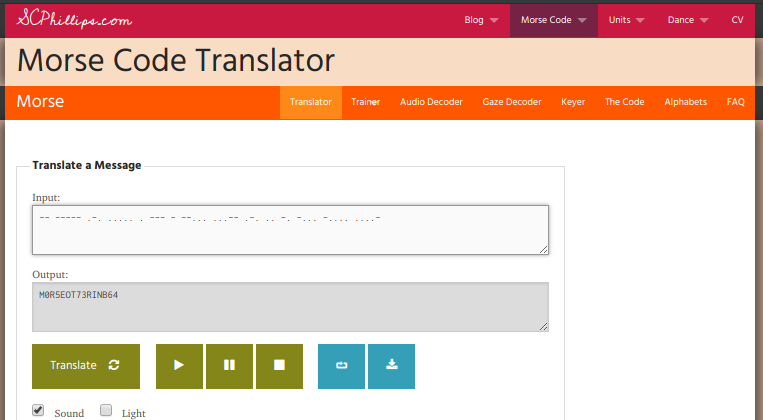
Added the missing parts from the flag in order to respect the format.